Add office photos
Premium Employer
Qualys
3.8
based on 217 Reviews
Company Overview
Company Locations
Working at Qualys
Company Summary
Qualys helps your business automate the full spectrum of auditing, compliance and protection of your IT systems and web applications.
Overall Rating
3.8/5
based on 217 reviews
3% above
industry average
Critically rated for
Promotions
Work Policy
Hybrid
90% employees reported
Monday to Friday
90% employees reported
Flexible timing
85% employees reported
No travel
90% employees reported
View detailed work policy
Top Employees Benefits
Cafeteria
5 employees reported
Health insurance
5 employees reported
Job/Soft skill training
3 employees reported
Office cab/shuttle
2 employees reported
View all benefits
About Qualys
Founded in1999 (26 yrs old)
India Employee Count1k-5k
Global Employee Count1k-5k
India HeadquartersPune, Maharashtra, India
Office Locations
Websitequalys.com
Primary Industry
Other Industries
Are you managing Qualys's employer brand? To edit company information,
claim this page for free
Qualys, Inc. is a pioneer and leading provider of disruptive cloud-based security, compliance and IT solutions with more than 10,000 subscription customers worldwide, including a majority of the Forbes Global 100 and Fortune 100. Qualys helps organizations streamline and automate their security and compliance solutions onto a single platform for greater agility, better business outcomes, and substantial cost savings.
The Qualys Cloud Platform leverages a single agent to continuously deliver critical security intelligence while enabling enterprises to automate the full spectrum of vulnerability detection, compliance, and protection for IT systems, workloads and web applications across on premises, endpoints, servers, public and private clouds, containers, and mobile devices. Founded in 1999 as one of the first SaaS security companies, Qualys has strategic partnerships and seamlessly integrates its vulnerability management capabilities into security offerings from cloud service providers, including Amazon Web Services, the Google Cloud Platform and Microsoft Azure, along with a number of leading managed service providers and global consulting organizations.
The Qualys Cloud Platform leverages a single agent to continuously deliver critical security intelligence while enabling enterprises to automate the full spectrum of vulnerability detection, compliance, and protection for IT systems, workloads and web applications across on premises, endpoints, servers, public and private clouds, containers, and mobile devices. Founded in 1999 as one of the first SaaS security companies, Qualys has strategic partnerships and seamlessly integrates its vulnerability management capabilities into security offerings from cloud service providers, including Amazon Web Services, the Google Cloud Platform and Microsoft Azure, along with a number of leading managed service providers and global consulting organizations.
Managing your company's employer brand?
Claim this Company Page for FREE
Qualys Ratings
based on 217 reviews
Overall Rating
3.8/5
How AmbitionBox ratings work?
5
80
4
58
3
36
2
12
1
31
Category Ratings
3.7
Salary
3.6
Skill development
3.5
Company culture
3.5
Job security
3.5
Work-life balance
3.5
Work satisfaction
3.3
Promotions
Qualys is rated 3.8 out of 5 stars on AmbitionBox, based on 217 company reviews.This rating reflects an average employee experience, indicating moderate satisfaction with the company’s work culture, benefits, and career growth opportunities. AmbitionBox gathers authentic employee reviews and ratings, making it a trusted platform for job seekers and employees in India.
Read more
Gender Based Ratings at Qualys
based on 202 reviews
4.1
Rated by 33 Women
Rated 4.0 for Salary and 3.9 for Skill development
3.8
Rated by 169 Men
Rated 3.6 for Work-life balance and 3.6 for Salary
Work Policy at Qualys
based on 32 reviews in last 6 months
Hybrid
90%
Work from office
10%
Qualys Reviews
Top mentions in Qualys Reviews
+ 5 more
Compare Qualys with Similar Companies
Change Company | Change Company | Change Company | ||
|---|---|---|---|---|
Overall Rating | 3.8/5 based on 217 reviews | 4.0/5 based on 262 reviews | 1.8/5 based on 9 reviews | 2.0/5 based on 1 reviews |
Highly Rated for | No highly rated category | Work-life balance Company culture Skill development | Salary | No highly rated category |
Critically Rated for | Promotions | No critically rated category | Work-life balance Job security Work satisfaction | Skill development Work-life balance Salary |
Primary Work Policy | Hybrid 90% employees reported | Permanent work from home 51% employees reported | - | - |
Rating by Women Employees | 4.1 Good rated by 33 women | 3.7 Good rated by 65 women | - no rating available | - no rating available |
Rating by Men Employees | 3.8 Good rated by 169 men | 4.2 Good rated by 176 men | - no rating available | - no rating available |
Job security | 3.5 Good | 3.6 Good | 1.5 Bad | - Data not available |
View more
Qualys Salaries
Qualys salaries have received with an average score of 3.7 out of 5 by 217 employees.
Software Engineer
(145 salaries)
Unlock
₹5 L/yr - ₹17.3 L/yr
Senior Software Engineer
(141 salaries)
Unlock
₹10.5 L/yr - ₹35 L/yr
Lead Software Engineer
(61 salaries)
Unlock
₹27.2 L/yr - ₹41 L/yr
Site Reliability Engineer
(48 salaries)
Unlock
₹4 L/yr - ₹16.6 L/yr
Senior QA Engineer
(39 salaries)
Unlock
₹11 L/yr - ₹20 L/yr
Senior Software QA Engineer
(38 salaries)
Unlock
₹12 L/yr - ₹27.6 L/yr
Technical Support Engineer
(33 salaries)
Unlock
₹5.4 L/yr - ₹13 L/yr
Software QA Engineer
(31 salaries)
Unlock
₹6.9 L/yr - ₹15 L/yr
Lead QA Engineer
(26 salaries)
Unlock
₹17.9 L/yr - ₹41 L/yr
Devops Engineer
(23 salaries)
Unlock
₹6.3 L/yr - ₹14 L/yr
Qualys Jobs
Popular Designations Qualys Hires for
Current Openings
Qualys News
View all
Steps to TruRisk – 1: Shift to Priority-Driven Strategies
- Security and IT teams facing overwhelming alerts and breaches despite patching efforts necessitate prioritizing high-risk vulnerabilities to address root causes effectively.
- The rise in high-to-critical vulnerabilities underscores the need for organizations to rethink security strategies and focus on what truly matters.
- Organizations must shift towards risk-based prioritization to tackle critical vulnerabilities rather than treating all vulnerabilities equally.
- A one-size-fits-all approach to patching can lead to inefficiencies, unnecessary downtime, and inadequate protection for critical systems.
- Prioritization, guided by risk tolerance and critical asset identification, is crucial for effective risk reduction and resource allocation.
- Aligning security efforts with business priorities and quantifying risk in business terms is essential for meaningful risk reduction.
- Adopting a unified risk approach and a shared risk language enhances efficiency, consistency, and resilience in cybersecurity operations.
- Embedding security strategies into business operations and using a risk-based approach can transform cybersecurity into a scalable, precision-driven system.
- The concept of Risk = Likelihood x Impact forms the basis for clear strategy and a shared risk language in cybersecurity.
- TruRisk integrated into Qualys VMDR 2.0 provides a measurable and actionable component for prioritizing vulnerabilities based on risk calculation.
Qualys | 10 Mar, 2025

How Qualys Policy Compliance Helps You Adopt NIST AI RMF 1.0
- AI technologies are rapidly changing industries, bringing both opportunities and risks.
- The NIST AI Risk Management Framework (RMF 1.0) helps organizations manage AI risks effectively.
- Qualys Policy Compliance supports NIST AI RMF adoption by automating policy adherence.
- NIST AI RMF focuses on trustworthy AI through mapping, measuring, managing, and governing AI risks.
- Qualys addresses challenges in NIST AI RMF adoption such as compliance complexity and risk visibility.
- Qualys Policy Compliance simplifies AI risk management by providing real-time monitoring and automation.
- It helps organizations map AI risks, measure them in real time, manage with automation, and govern with confidence.
- Key benefits of Qualys Policy Compliance include streamlined compliance, enhanced risk visibility, and adaptable governance.
- By leveraging Qualys Policy Compliance, organizations can mitigate AI risks and enhance accountability in AI systems.
- Start your journey towards NIST AI RMF adoption with Qualys Policy Compliance for trustworthy AI.
Qualys | 4 Mar, 2025

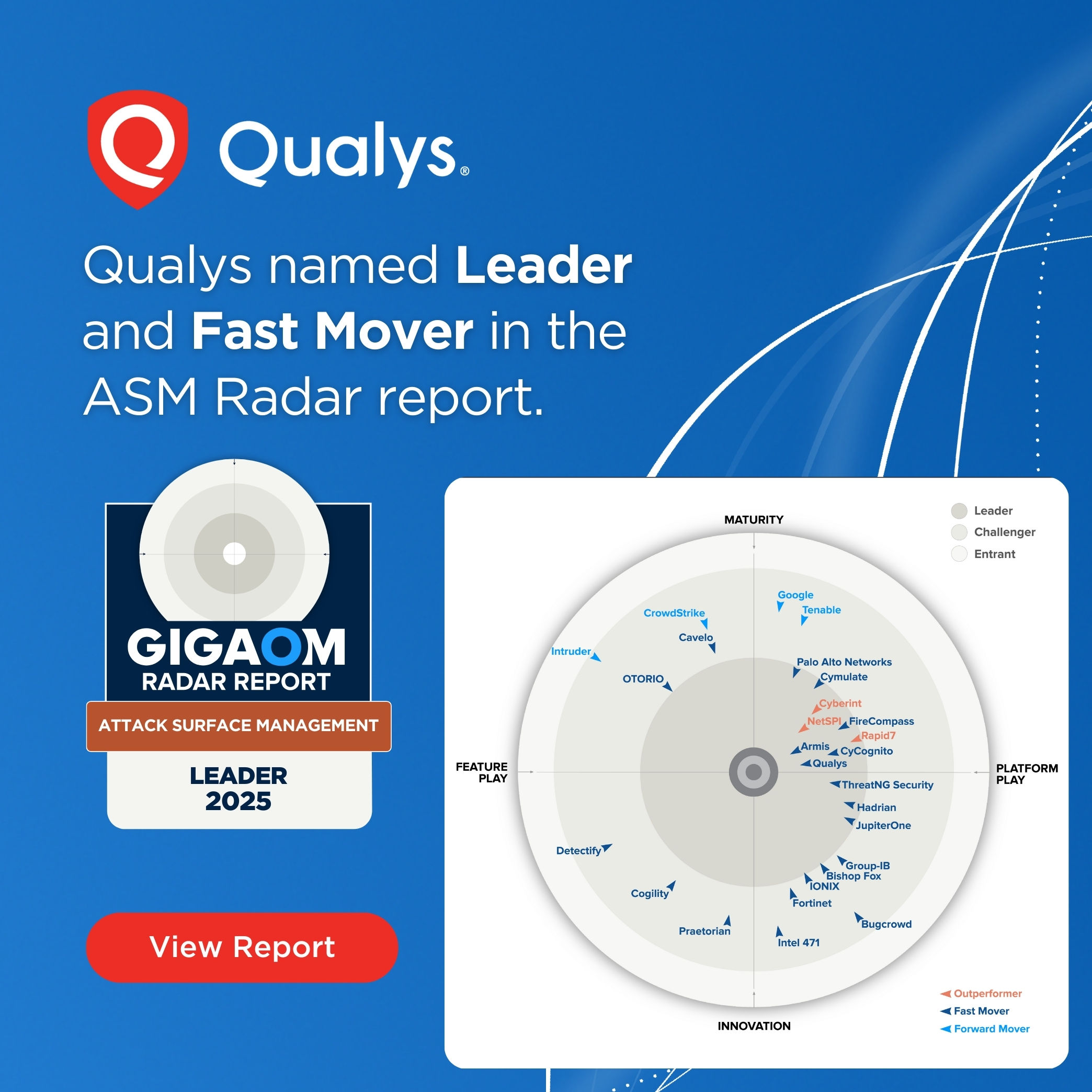
Independent Analyst Firm: Qualys Recognized as a Leader in Attack Surface Management
- Qualys has been recognized as a leader in Attack Surface Management (ASM) by GigaOm, highlighting its visionary offering CyberSecurity Asset Management (CSAM).
- The ASM market emphasizes the integration of internal and external attack surface monitoring, threat intelligence, and asset discovery.
- GigaOm recognized Qualys for excelling in risk scoring, asset correlation, and comprehensive asset visibility.
- Qualys was positioned as a Leader and Fast Mover in the Maturity/Platform Play quadrant of the ASM Radar report.
- The evaluation criteria included comprehensive asset discovery, risk scoring, attack path analysis, and coverage of internal, external, and third-party risks.
- Qualys stands out for its strong performance in discovery, risk assessment, and scalability across hybrid environments.
- The TruRisk prioritization engine by Qualys provides precise risk scoring based on various factors, distinguishing it from competitors.
- Qualys caters to enterprise environments with its platform supporting complex infrastructures and customizable scanning intervals.
- The report underlines Qualys' incremental advancements in stability, performance, compliance reporting, and integration capabilities.
- Qualys envisions ASM as the foundation for the Risk Operations Center, aligning with the market's direction towards unified risk management.
Qualys | 28 Feb, 2025
Defense Lessons From the Black Basta Ransomware Playbook
- The cybersecurity world was shocked by a massive leak of Black Basta's internal communications revealing their attack tactics, operations, and leadership.
- Lessons learned from the leak include the importance of immediate patching, tighter access controls, and rapid incident response to strengthen defenses against ransomware threats.
- Black Basta exploits vulnerabilities like exposed RDP servers, weak authentication mechanisms, and malware droppers to breach systems, emphasizing the need for organizations to understand their playbook.
- The ransomware group actively targets vulnerabilities such as exposed RDP and VPN services, known CVEs, and uses malware droppers to deliver payloads.
- A list of Top 20 CVEs actively exploited by Black Basta is provided, urging IT security professionals to patch these vulnerabilities immediately to prevent potential attacks.
- Critical misconfigurations that should be fixed immediately, including SMBv1 enabled systems, default credentials, weak VPN configurations, and exposed RDP, are highlighted as key vulnerabilities exploited by Black Basta.
- Black Basta's tactics involve a layered approach of credential theft, service exploitation, social engineering, and persistence, accelerating from initial access to network-wide compromise swiftly.
- Automated scripts are used post-exploitation to dump credentials, disable security tools, and deploy ransomware quickly, emphasizing the need for proactive detection and response measures.
- Qualys offers solutions to align with the recommendations to detect and mitigate Black Basta's tactics, leveraging CyberSecurity Asset Management, Patch Management, and VMDR for vulnerability detection and prioritization.
- Qualys Query Language (QQL) can help identify assets exposed to ransomware-targeted CVEs, misconfigurations, and security gaps, enabling faster remediation and risk-based prioritization against evolving threats like Black Basta.
Qualys | 26 Feb, 2025

Qualys TotalCloud KCS Achieves Red Hat Vulnerability Scanner Certification
- Qualys TotalCloud Kubernetes and Container Security (KCS) has achieved the Red Hat Vulnerability Scanning Certification, reinforcing commitment to accurate vulnerability detection.
- Qualys TotalCloud KCS integrates Red Hat's official security intelligence and multiple security feeds to provide relevant and actionable insights on vulnerabilities across Red Hat containers, images, and workloads.
- The certification ensures zero noise and guesswork in vulnerability reports, as well as instant access to Red Hat-approved patches for streamlined remediation.
- Qualys TotalCloud KCS simplifies security operations, enhances detection accuracy, and helps enterprises maintain compliance and reduce risk.
Qualys | 25 Feb, 2025

Overcoming Critical AI Security Risks Uncovered in DeepSeek-R1
- Security researchers have uncovered critical vulnerabilities in DeepSeek-R1, raising concerns for enterprise adoption.
- The security analysis conducted by Qualys revealed that DeepSeek-R1 failed 61% of the assessments and 58% of the jailbreak attempts, exposing ethical, legal, and operational risks.
- The vulnerabilities in DeepSeek-R1 pose significant risks for enterprises, including ethical violations, privacy and security breaches, and compliance concerns.
- To strengthen AI security, organizations are advised to prioritize technical safeguards, conduct adversarial testing, and ensure compliance with data protection regulations.
Cybersecurity-Insiders | 25 Feb, 2025

From Vulnerability Scanning to Risk Management: The Complete VMDR Advantage
- Vulnerability management is about managing risk beyond just scanning for vulnerabilities, as per CISA and Forrester reports.
- Qualys VMDR offers a leading risk-based vulnerability management solution, aiding in visibility, prioritization, and faster risk remediation.
- VMDR goes beyond traditional tools, combining asset discovery, prioritization, compliance benchmarking, and real-time threat intelligence.
- Qualys VMDR helps in addressing the dynamic attack surface, ensuring effective vulnerability scanning and prioritization.
- VMDR provides capabilities like TruRisk for quantifying risk, MITRE ATT&CK mapping for defense strategies, and SwCA for software composition analysis.
- With access to real-time threat intelligence, VMDR enables proactive identification and response to emerging cyber threats.
- VMDR enhances risk detection, scoring, and prioritization, helping organizations maintain a strong security posture.
- The platform offers features like global asset view, certificate inventory, cloud agents, and compliance assessment to ensure comprehensive security coverage.
- Qualys VMDR can integrate with ITSM tools like ServiceNow and issue tracking systems like JIRA for streamlined risk communication and remediation workflows.
- The system also provides a standard API for seamless integrations with custom solutions and third-party tools, allowing organizations to enhance their vulnerability management efforts.
Qualys | 25 Feb, 2025

Qualys Adds Threat Intelligence for Typosquatting and Defamatory Domains to External Attack Surface Management
- Qualys has added typosquatting and defamatory domain detection to reduce cyber risks from credential harvesting, phishing, and malware downloads.
- Typosquatting involves registering similar domains to trick users into entering sensitive data and credentials.
- Defamatory domains are registered to harm an organization's reputation by hosting negative content.
- Qualys' CSAM with EASM offers automated detection of these malicious domains, helping organizations stay ahead of cyber threats.
Qualys | 13 Feb, 2025

When you shouldn’t patch: Managing your risk factors
- Patching for known vulnerabilities is a standard practice in cybersecurity, but there are times when it is better not to patch, according to experts at Qualys QSC24 conference.
- Chief Technology Officer Dilip Bachwani advises that not all vulnerabilities need immediate fixing, especially if they do not apply to your organization's environment.
- Security teams are urged to evaluate their risk thresholds before automatically installing every new patch to prevent cyber incidents.
- Prioritizing vulnerabilities is crucial as the number of common vulnerabilities and exposures (CVEs) continues to rise rapidly each year.
- Qualys researchers recommend identifying and monitoring the attack surface to prioritize what vulnerabilities require immediate patching based on risk.
- An attack surface management program is essential to monitor all assets across the organization and ensure proper protection of critical systems.
- Patching protocols should be tailored to each organization's risk tolerance, with some cases where slowing down or skipping patching is advised based on specific circumstances.
- Factors like ongoing projects, reports of patch bugs, isolated vulnerable software, and cost-benefit analyses can influence the decision to delay or forgo patching.
- Maintaining good cybersecurity hygiene can potentially lower cybersecurity insurance costs, even if organizations choose not to patch every vulnerability.
- Ultimately, the decision to patch or not patch should be based on the business value and risk tolerance of the organization, balancing the need to address critical vulnerabilities with accepting some level of risk.
Securityintelligence | 12 Feb, 2025

Microsoft Patch Tuesday, February 2025 Security Update Review
- Microsoft's February 2025 Patch Tuesday included crucial updates addressing 67 vulnerabilities, with 3 critical and 53 important severity ones.
- The updates covered zero-day vulnerabilities, including those actively exploited and publicly disclosed.
- Ten vulnerabilities in Microsoft Edge (Chromium-based) were addressed in the latest updates.
- Various software vulnerabilities were patched, including Spoofing, Denial of Service, Elevation of Privilege, Information Disclosure, and Remote Code Execution.
- The vulnerabilities were categorized under different types such as Spoofing, Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, and Security Feature Bypass.
- Critical severity vulnerabilities in the update included issues like DHCP Client Service Remote Code Execution and Windows LDAP Remote Code Execution.
- Some vulnerabilities required specific conditions for successful exploitation, like gaining SYSTEM privileges or executing remote code.
- Microsoft's release covered various products like Excel, SharePoint, Windows Core Messaging, and others, with potential risks of privilege escalation and code execution.
- The next Patch Tuesday is scheduled for March 11, promising more details and analysis, while urging users to stay secure and subscribe to relevant webinars for vulnerability insights.
- Qualys hosts monthly webinars to aid customers in managing vulnerabilities efficiently, emphasizing the importance of patch management and timely remediation.
Qualys | 12 Feb, 2025

Powered by
Qualys Offices
Compare Qualys with

Gen
4.0

FireEye
4.3

CrowdStrike
4.1

Palo Alto Networks
3.9

Check Point Software Technologies
3.8

Fortinet
4.2

CyberArk
3.7

Xoriant
4.1

Photon Interactive
4.0

CitiusTech
3.4

Iris Software
4.0

HTC Global Services
3.5

HERE Technologies
3.9

iOPEX Technologies
3.5

Tietoevry
4.3

Collabera Technologies
3.5

Evalueserve
3.2

Unisys
3.6

Infogain
3.6

Slk Software Services
3.3
Edit your company information by claiming this page
Contribute & help others!
You can choose to be anonymous
Companies Similar to Qualys

FireEye
Hardware & Networking, IT Services & Consulting
4.3
• 41 reviews

CrowdStrike
Internet, IT Services & Consulting
4.1
• 78 reviews

Palo Alto Networks
Hardware & Networking, IT Services & Consulting
3.9
• 94 reviews

Check Point Software Technologies
Hardware & Networking, Software Product
3.8
• 40 reviews

Xoriant
IT Services & Consulting, Software Product
4.1
• 1.9k reviews

Photon Interactive
IT Services & Consulting
4.0
• 1.8k reviews
Qualys FAQs
When was Qualys founded?
Qualys was founded in 1999. The company has been operating for 26 years primarily in the IT Services & Consulting sector.
Where is the Qualys headquarters located?
Qualys is headquartered in Pune, Maharashtra and has an office in Pune
How many employees does Qualys have in India?
Qualys currently has more than 2,500+ employees in India. Engineering - Software & QA department appears to have the highest employee count in Qualys based on the number of reviews submitted on AmbitionBox.
Does Qualys have good work-life balance?
Qualys has a Work-Life Balance Rating of 3.5 out of 5 based on 200+ employee reviews on AmbitionBox. 64% employees rated Qualys 4 or above, while 36% employees rated it 3 or below on work-life balance. This indicates that the majority of employees feel a generally balanced work-life experience, with some opportunities for improvement based on the feedback. We encourage you to read Qualys work-life balance reviews for more details
Is Qualys good for career growth?
Career growth at Qualys is rated as moderate, with a promotions and appraisal rating of 3.3. 36% employees rated Qualys 3 or below, while 64% employees rated it 4 or above on promotions/appraisal. This rating suggests that while some employees view growth opportunities favorably, there is scope for improvement based on employee feedback. We recommend reading Qualys promotions/appraisals reviews for more detailed insights.
What are the cons of working in Qualys?
Working at Qualys does have some drawbacks that potential employees should consider. The company is poorly rated for promotions / appraisal, based on 200+ employee reviews on AmbitionBox.
Stay ahead in your career. Get AmbitionBox app

Helping over 1 Crore job seekers every month in choosing their right fit company
75 Lakh+
Reviews
5 Lakh+
Interviews
4 Crore+
Salaries
1 Cr+
Users/Month
Contribute to help millions
Get AmbitionBox app


